I’ve really grown to like the look of the blue and white Power Mac G3 tower lately, and really felt the need to have one as a daily driver. In the looks department anyways. This spawned the idea of ATX-modding the case of said computer.
As luck would have it, I asked around on another forum, and one of the users there happened to have a nice condition one destined for the scrapyard. So it was picked up from death row for free, including an internal ZIP250-drive, new-old-stock keyboard and mouse. An ATX mod of a Power Mac G3
Notes

Wiz Research discovered CVE-2025-1097, CVE-2025-1098, CVE-2025-24514 and CVE-2025-1974, a series of unauthenticated Remote Code Execution vulnerabilities in Ingress NGINX Controller for Kubernetes dubbed #IngressNightmare. Exploitation of these vulnerabilities leads to unauthorized access to all secrets stored across all namespaces in the Kubernetes cluster by attackers, which can result in cluster takeover. Critical Unauthenticated Remote Code Execution Vulnerabilities in Ingress NGINX
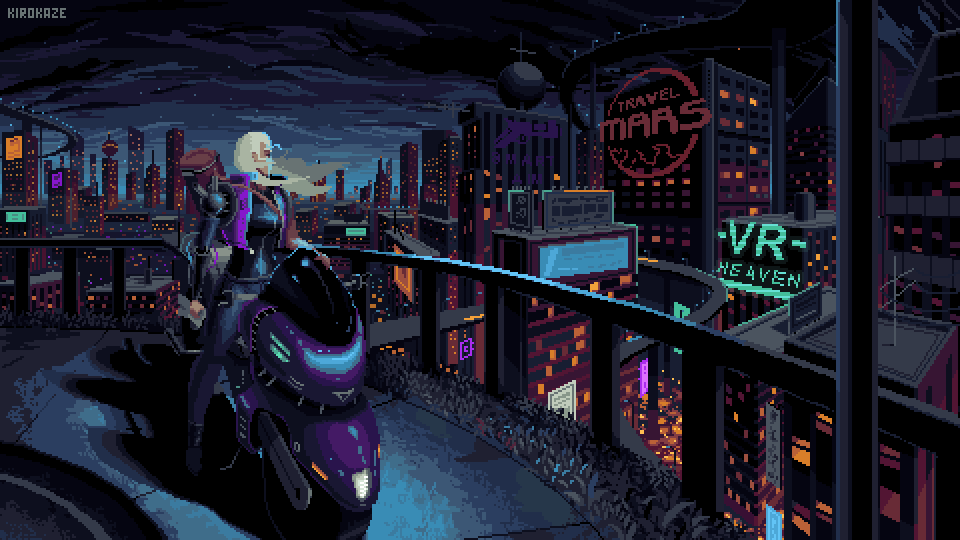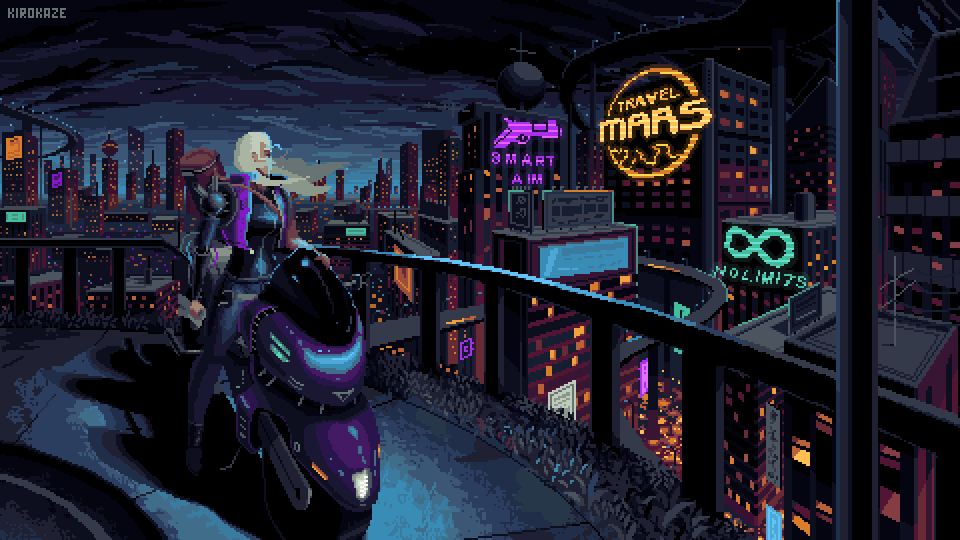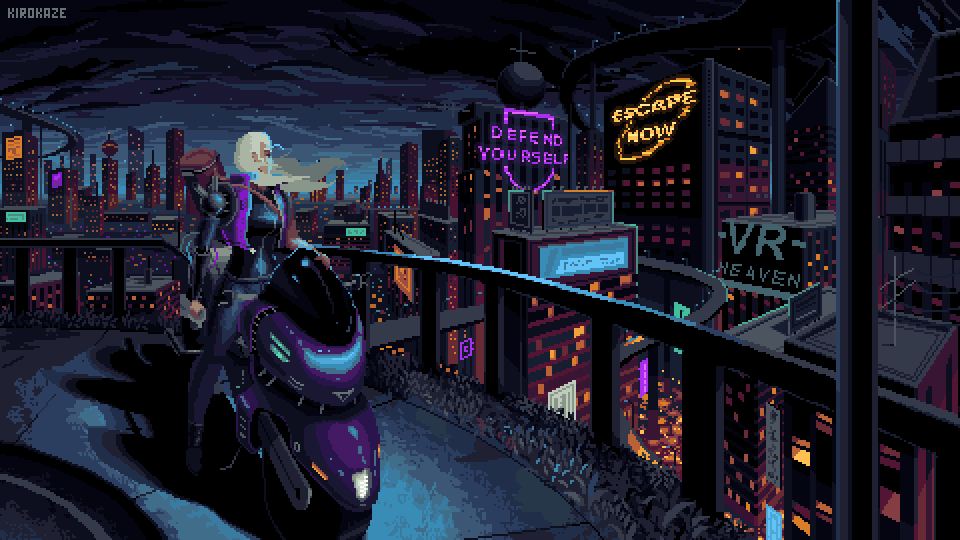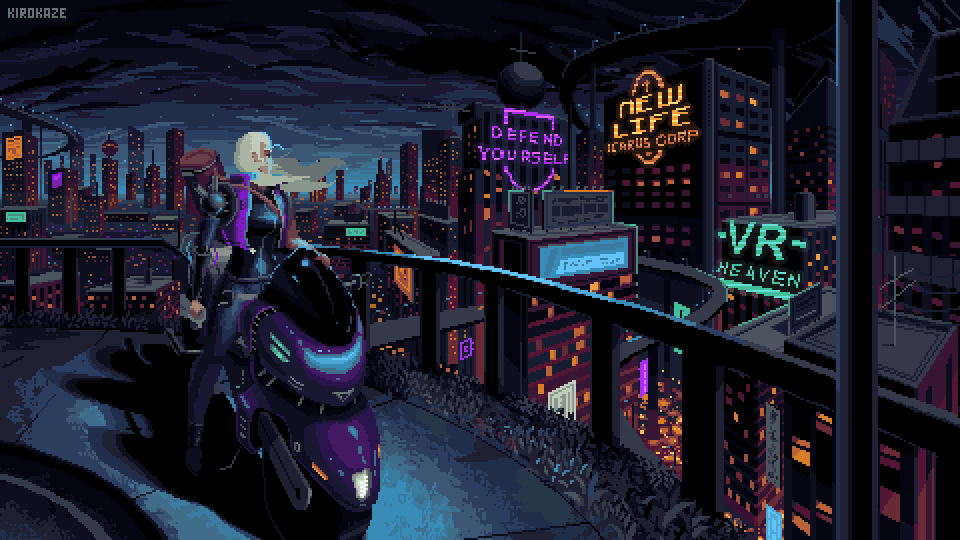
Not where I wanna be but not where I used to be.
This cheat sheet contains payloads for bypassing URL validation. These wordlists are useful for attacks such as server-side request forgery, CORS misconfigurations, and open redirection. URL validation bypass cheat sheet
→ in reply to @note#1742666804
Can you read thoughts, can you read palms?
Can you predict the future, can you see storms coming?
Can you read signs, can you read stars?
Can you make peace, can you fight war?
Can you milk cows, even though you drive cars
Huh, can you survive, against all odds, now?
No matter what, we’ll survive it
What’s hue? What’s man? What’s human?
Anything along the land we consuming
Eatin’, deletin’, ruin
Trying to get paper (What?)
Gotta have land, gotta have acres
So I can sit back like Jack Nicholson
Watch niggers play the game like the Lakers.
This a vulnerability in the HFS+ driver of the Linux kernel. Interestingly, the vulnerability has always been present in the kernel tree since the initial git repository build 1da177 in 2005, that is, since Linux-2.6.12-rc2.
HFS+ had been the primary Mac OS X file system until it was replaced with the Apple File System (APFS), released with macOS High Sierra in 2017. It is based on B-tree data structures and is well documented. The vulnerability itself is a buffer overflow in B-tree node processing. Under certain circumstances, the function hfs_bnode_read_key found in fs/hfsplus/bnode.c is used to populate an in-kernel buffer from the filesystem, and the function itself does not check for boundary conditions regarding the size of the key. Linux kernel hfsplus slab-out-of-bounds Write
This blog post will analyse the exploitability of the temporal safety vulnerabilities in Nginx AIxCC.
AIxCC is a DARPA competition to find vulnerabilities in codebases using AI. The competitors are not looking for 0-days but rather intentionally added vulnerabilities in existing codebases. One of them was Nginx in the semifinals, which already took place.
In this blog post, I will have a different focus on whether these added vulnerabilities can be exploited to achieve more than just crashes. Exploitation of AIxCC Nginx bugs
A critical vulnerability has been identified in MegaRAC Baseboard Management Controller (BMC) software, developed by American Megatrends International (AMI), enabling attackers to seize control over servers and potentially render them inoperable.
MegaRAC BMC is a remote server management platform that enables administrators to oversee hardware without physical access. This technology is widely utilized across server products from over ten major vendors, including HPE, Asus, ASRock, and various other providers catering to cloud infrastructures and data centers. CVE-2024-54085: Critical BMC Flaw Exposes Servers to Total Takeover

Japanese R-rated movie about random people meeting for sex. If you always wanted to attend a sex party and never did, this is the movie to watch.

The story of a samurai who requests to commit harakiri.
After all, this thing we call samurai honor is ultimately nothing but a facade.
It occurs to me that nobody cares about discussion anymore. Sure people are more than happy to talk but that’s just half of the equation, you have to be able to listen too.
It seems as though that even in the rare occasion that a person can deign to listen to another almost never will they really hear them, sure they’ll go through the motions they will maintain eye contact and nod at the appropriate moments, every now and again make a confirmative noise to assure the other that they understand that every word has passed from tongue to ear without incident but this is nothing but a farce, a hollow performance one does while internally counting each second until next they can vomit their own proclamations to their unsuspecting victim, ignorant of what their partner has said and all the happier for it.
People of the modern era have developed an impressive resilience of the mind preventing all alien ideas from penetrating it while also maintaining a animalistic killer instinct to destroy all ideas of their competitors, there can be no room for compromise, no show of weakness, such is the law of the jungle, such is the law of contemporary discourse because if you were to give an inch they would take a mile, so you must seize the very land beneath them before they can. For all our lives we remain imprisoned within our own heads only capable of communicating with our fellow jailbirds through a limited and convoluted system of sounds ill fit to express the concepts they represent. The last thing such a fragile setup needs is to be weighed down by complications.
Their are millions of people in this world that talk to each other every day, but I do not think I have ever had a single conversation with any of them, I think that one day I might like to.
When a specially crafted .library-ms file containing an SMB path is compressed within a RAR/ZIP archive and subsequently extracted, Windows Explorer automatically parses the contents of this file due to its built-in indexing and preview mechanism. This behavior occurs because Windows Explorer processes certain file types automatically upon extraction to generate previews, thumbnails, or index metadata, even if the file is never explicitly opened or clicked by the user.
The .library-ms file format is XML-based and is trusted by Windows Explorer to define search and library locations. Upon extraction, the indexing service and Explorer’s built-in file parsing mechanism immediately analyze the .library-ms file content to render appropriate icons, thumbnails, or metadata information. CVE-2025-24071: NTLM Hash Leak via RAR/ZIP Extraction and .library-ms File
I’m convinced we’re all just subconsciously, living-out archetypes. Be it to fit in or otherwise belong to this world, we conform and limit what we can be to what has been. Only the truly insane stand a chance of flourishing and breaking free.
A rootkit is malware whose main objective and purpose is to maintain persistence within a system, remain completely hidden, hide processes, hide directories, etc., in order to avoid detection.
This makes its detection very complex, and its mitigation even more complex, since one of the main objectives of a rootkit is to remain hidden.
A rootkit, it changes the system’s default behavior to what it wants. The Art of Linux Kernel Rootkits
I recently pulled out my old childhood Game Boy Color from a drawer to play around with it. The idea is to use LSDJ to accompany LARS. Unfortunately I kinda forgot how bad the GBC screen is, without any backlight.
So I looked around AliExpress a bit and found the store of HISPEEDIDO. They offer many nice modding kits for old consoles, so I got the OLED screen and USB-C battery replacements. Game Boy Color modding and experiments
Enlightenment in this day and age is realising the following:
- History repeats itself.
- Politics are meaningless and pointless to participate in.
- Majority of news is propaganda.
- The USA is essentially a lie.
- Buddhism is the only religion worth a damn.
- Deism and agnosticism are the two non-religion belief-systems that are worth adopting.
There are two types of people in this world.
























