Notes
Linux vulnerability called Dirty Pipe, CVE-2022-0847, appeared in kernel version 5.8 and fixed in versions 5.16.11, 5.15.25 and 5.102. Working exploit here.
The new generation of the Starlink terminal was released at the end of 2021. Dishy antenna is square now, and a completely redesigned indoor unit combines WiFi router and power supply. The new design should be more cost-effective, so there is no AUX Ethernet port on the router, only WiFi. Later SpaceX released an official Ethernet adapter that brings up the port back.
Russian National Coordination Center for Computer Incidents (NKTsKI) releases a list of ~17k IPs that are probably DDoSing Russian infrastructure. And as bonus, another list containing attackers’ referrer domain information. Those “people” that were DDoSing the FSB website using their residential Internet connection are crème de la crème.
Referrer information can definitely be spoofed but it’s funny seeing FBI and CIA domains in there.
If your RSS reader is still pointed to the old RSS feed for notes, please update it to the new RSS feed. Thanks.
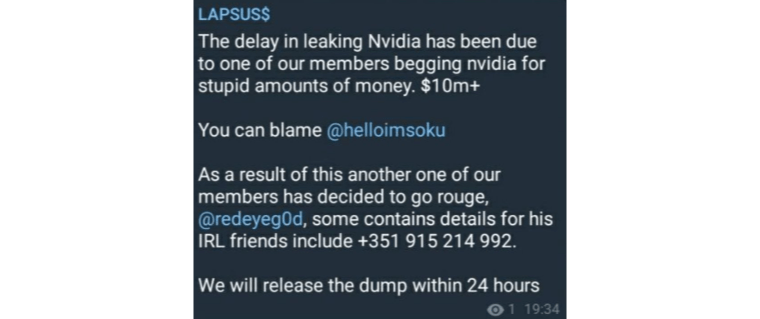
If you’re interested in the NVIDIA leak (it clocks at about 20GB of data, so make sure you have the space for it), here is a magnet for it:
magnet:?xt=urn:btih:DC718539145BDE27DDDB5E94C67949E6D1C8513C&dn=integdev_gpu_drv.rar&tr=udp%3a%2f%2ftracker.openbittorrent.com%3a80%2fannounce&tr=udp%3a%2f%2ftracker.opentrackr.org%3a1337%2fannounce
Enjoy.
In early December, a healthcare provider in Canada was hit by two separate ransomware actors with very different tactics. The first ransomware group, identified as Karma, exfiltrated data but did not encrypt the target’s systems—because the targeted organization was in healthcare, they claimed in the ransom note dropped on the target’s PCs.
The second group, identified as Conti, came onto the network later, but had no such reservations. Less than a day after the Karma gang dropped their ransom notes, the Conti actors deployed their ransomware. Sophos’ Rapid Response team had just begun talking with the targeted company hours earlier, and the customer had not yet deployed Sophos’ software to the portion of the network where ransomware had been staged by the Conti gang.
↳ Conti and Karma actors attack healthcare provider at same time through ProxyShell exploits
In this repository you will find: Mindmaps, tips & tricks, resources and every thing related to API Security and API Penetration Testing. Our mindmaps and resources are based on OWASP TOP 10 API, our experience in Penetration testing and other resources to deliver the most advanced and accurate API security and penetration testing resource in the WEB!!

As a response to Western warmongering and American threats to use cyber warfare against the citizens of Russian Federation, the Conti Team is officially announcing that we will use our full capacity to deliver retaliatory measures in case the Western warmongers attempt to target critical infrastructure in Russia or any Russian-speaking region of the world. We do not ally with any government and we condemn the ongoing war. However, since the West is known to wage its wars primarily by targeting civilians, we will use our resources in order to strike back if the well being and safety of peaceful citizens will be at stake due to American cyber aggression. Conti Team (onion link)
Anony🐭 (you know, the cyber-armchair-warrior arm of the NSA) claimed they hacked the website of the Russian Ministry of Defense. In the distributed archive there was a copy of the VLC Player and a small selection of data from the gov.ru and mil.ru websites but from really old leaks. Twitter conveniently removed their post, of course. Get well, NSA! I mean Anonymouse. I think.
Repeat after me, journalists: DDoS attacks are not hacking. Thank you. Tune in for next episode when I will teach you that what comes around, goes around.
Cool list of MD5 hashes of adult sites to censor filter from the Firefox’s New Tab page. That’s the spirit, Mozilla. Go into irrelevance, godspeed.

Zenith is an exploit I wrote to compromise the TP-Link AC1750 Smart Wi-Fi Router which was part of the Routers / LAN category in the Pwn2Own Austin 2021 contest.
It exploits an integer overflow that results in a heap-buffer overflow in a kmalloc-128 slab cache in the NetUSB driver which is authored by the KCodes company. The driver listens on the br-lan interface on TCP port 20005 and parses attacker controlled data. It has been tested against the Archer C7(US)_V5_210519 firmware that was published on August 20 2021 (you can find the NetUSB.ko in TP-Link’s firmware images). TP-Link AC1750 Smart Wi-Fi Router Remote Code Execution Vulnerability
Search WiFi geolocation data by BSSID and SSID on different public databases.
↳ geowifi
Reconator is a Framework for automating your process of reconnaissance without any Computing resource (Systemless Recon) at free of cost. Its Purely designed to host on Heroku which is a free cloud hosting provider. It performs the work of enumerations along with many vulnerability checks and obtains maximum information about the target domain.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi and much more. Along with these, it performs OSINT, fuzzing, dorking, ports scanning, nuclei scan on your target.
Incident Response Documentation made easy. Developed by Incident Responders for Incident Responders. Aurora brings “Spreadsheet of Doom” used in the SANS FOR508 class to the next level. Having led many cases and taught so many students how to do IR right, I realized, that many struggle with keeping control over all the findings. That does not only prevent them from seeing what they already have, but even less so what they are missing.
It’s intended to be used in small and big incident response investigations to track findings, tasks, making reporting easy and generally stay on top of the game.
























