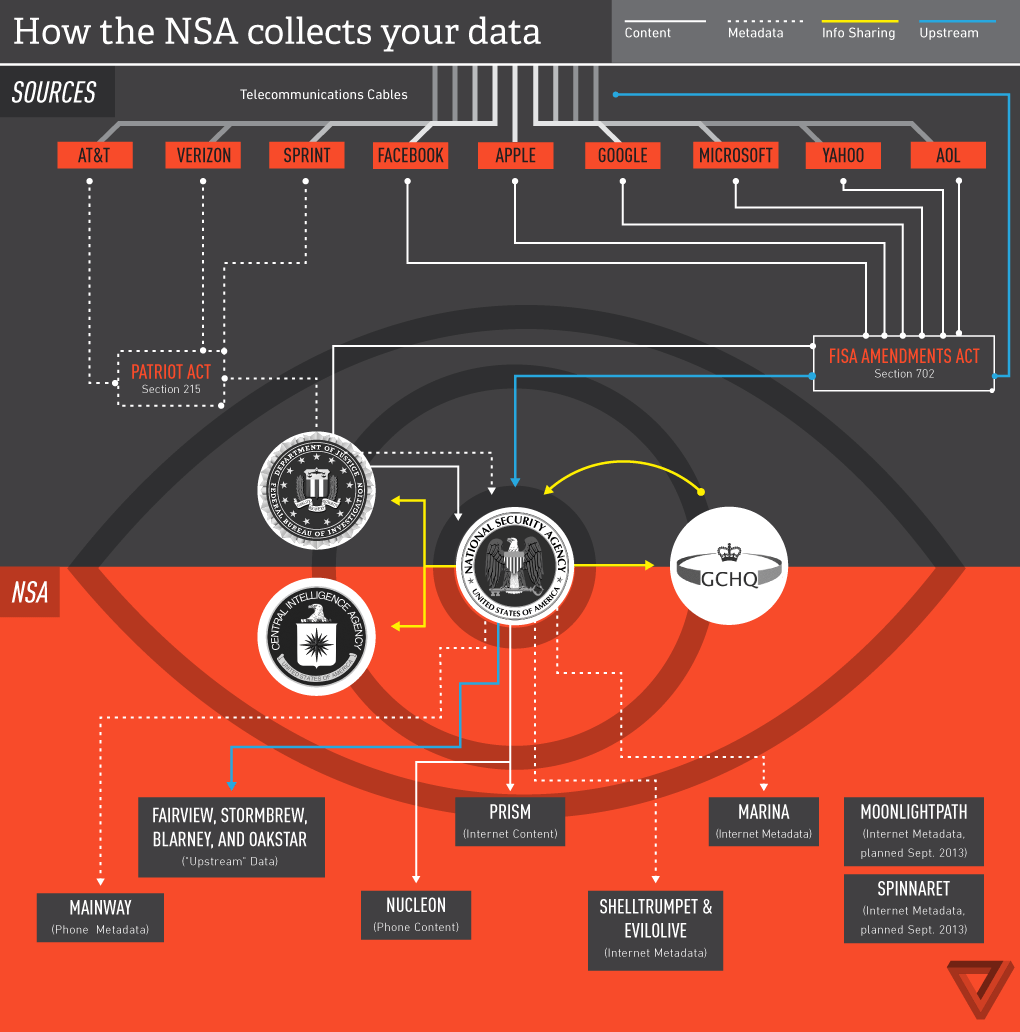
This report provides details for a vulnerability, CVE-2022-22292, discovered by Kryptowire that is present in various Samsung Android devices running Android versions 9, 10, 11, and 12. The vulnerability allows any local app on the device (including third-party apps with zero permissions) to provide arbitrary
Intentobjects that will be used by a pre-installed app (com.android.server.telecom) executing as the system user to start an activity app component (even those that are not exported) of the attacker’s choosing, affecting Android versions 10, 11, and 12.The same vulnerability is present on Android 9, although it allows zero-permission third-party apps to provide arbitrary
Intentobjects that are sent to broadcast receiver app components by the same vulnerable pre-installed app executing as thesystemuser (instead of being used to start arbitrary activity app components in more recent Android versions). This vulnerability allows a third-party app to provide arbitraryIntentobjects that will be started by a pre-installed app executing as thesystemuser with all its permissions, privileges, and capabilities. Start arbitrary activity app components as the system user vulnerability Affecting Samsung Android devices
Notes
Measurement SDK library (coelib.c.couluslibrary) implemented in various Android apps is responsible for collecting sensitive data such as Clipboard, GPS, Email, Phone Numbers, IMEI, SSID.
At this point, we wanted to figure out who owns
mobile.measurelib.com, which turned out to be rather difficult. We searched for strings that we saw in the network traffic to measurelib.com, such as ARPSurvey, measurelib, and ClientIPv4, to see which SDK was responsible for them. Yet, none that we sought were present! The app’s privacy policy was also unhelpful in identifying this traffic to measurelib.com: while listing other location and router data collectors like Huq, they somehow omitted measurelib.com.To find out more, we looked for other apps that talked to mobile.measurelib.com. We found a few, including Audio Quran, Qibla Compass, and a QR code scanner, all of which have location permissions. This means that if the user grants the app access to location data, then this SDK does not need a side channel to get the router’s MAC address. In such apps, when we performed our test, we found that they also shared precise GPS location information with measurelib.com, as well. The Curious Case of Coulus Coelib
Microsoft Azure Active Directory (Azure AD) is an identity and access management solution used by over 88 percent of Fortune 500 companies as of this publication. This market penetration makes Azure AD a lucrative target for threat actors. In the second half of 2021, Secureworks Counter Threat Unit (CTU) researchers analyzed Azure AD tenants and were able to extract open-source intelligence (OSINT) about organizations.
Threat actors frequently use OSINT to perform reconnaissance. CTU researchers identified several application programming interfaces (APIs) that access internal information of any organization that uses Azure AD. Collected details included licensing information, mailbox information, and directory synchronization status. Azure Active Directory Exposes Internal Information
A Remote Access Trojan or RAT is a tool used by Threat Actors (TAs) to gain full access and remote control on a user’s system, including mouse and keyboard control, files access, and network resources access.
During our regular OSINT research, Cyble Research Labs came across a new Remote Access Trojan (RAT) named Borat. Unlike other RATs, the Borat provides Ransomware, DDOS services, etc., to Threat Actors along with usual RAT features, further expanding the malware capabilities. Deep Dive Analysis – Borat RAT
There’s no Hell to fear below, but its prospect is in demand.
A guide covering Security including the applications, libraries and tools that will make you better and more efficient at securing your system operations and networks. Open Source Security Guide
My dad died, and my grandfather died, and my great-grandfather died. And the guy before him, I don’t know. Probably died. Norm MacDonald
What data do the Google Dialer and Messages apps on Android send to Google?
by Douglas J. Leith
Several threat actors have taken advantage of the war in Ukraine to launch a number of cyber attacks. The Malwarebytes Threat Intelligence team is actively monitoring these threats and has observed activities associated with the geopolitical conflict.
More specifically, we’ve witnessed several APT actors such as Mustang Panda, UNC1151 and SCARAB that have used war-related themes to target mostly Ukraine. We’ve also observed several different wipers and cybercrime groups such as FormBook using the same tactics. Beside those known groups we saw an actor that used multiple methods to deploy a variants of Quasar Rat. These methods include using documents that exploit CVE-2017-0199 and CVE-2021-40444, macro-embedded documents, and executables. New spear phishing campaign targets Russian dissidents
If you need a public DNS resolver you can use Njal.la DNS.
For IPv4:
95.215.19.53
For IPv6:
2001:67c:2354:2::53
You can use DNS-over-HTTPS with Mozilla Firefox and Thunderbird too.
In Firefox open the about:config page and change network.trr.mode to 2 to use DNS Over HTTPS but keep regular DNS as a fallback. Change network.trr.uri to https://dns.njal.la/dns-query too.
In Thunderbird open Preferences, General tab, scroll down and press the Config Editor button. Change network.trr.mode to 2 (same reason as Firefox above) and update network.trr.custom_uri, network.trr.default_provider_uri and network.trr.uri to https://dns.njal.la/dns-query too.
Today we are releasing versions 14.9.2, 14.8.5, and 14.7.7 for GitLab Community Edition (CE) and Enterprise Edition (EE). Please note, this critical release will also serve as our monthly security release for March.
We strongly recommend that all GitLab installations be upgraded to one of these versions immediately.
These versions contain important security fixes. GitLab.com is already running the patched version. GitLab Critical Security Release: 14.9.2, 14.8.5, and 14.7.7
As a side-note, nazi, communism, genocide, war crimes, human rights, they all lost their meaning. Now they’re just buzzwords peppered into the discourse around whatever current boogeyman is.
The Western society is on the way of banning the letter Z from the alphabet. They should start burning the books too.
The American companies Apple and Meta have transferred user information to hackers who forged an official request from law enforcement agencies.
In mid-2021, American companies provided some customer data, including address, phone number and IP address, after receiving fake “emergency information requests”.
Sources explained that usually requests for personal data are satisfied only if there is a search warrant or a court summons, but emergency requests do not require a court decision.
The illegally obtained data could in theory be used by social engineers to facilitate financial fraud schemes and other purposes. How much data fell into the clutches of hardened attackers remains a secret.
Laboratory for automated deployment of ESXi-based virtual machines, focused on DFIR and SOC. Lab-DFIR-SOC
Updated, it’s confirmed now.
As the world’s most popular Java lightweight open-source framework, Spring allows developers to focus on business logic and simplifies the development cycle of Java enterprise applications.
However, in the JDK9 version (and above) of the Spring framework, a remote attacker can obtain the
AccessLogValveobject and malicious field values through the parameter binding function of the framework on the basis of meeting certain conditions, thereby triggering the pipeline mechanism and writing arbitrary fields. SpringShell: Spring Core RCE 0-day Vulnerability - Image
An unconfirmed, but probable, remote code execution vulnerability is believed to exist in Spring, an extremely popular Java framework. This issue is likely easily exploited in common configurations. If confirmed, another notice will be sent out with a severity of ‘critical’. While unconfirmed, the severity has been assigned ‘high’.
Looks serious if confirmed.
→ in reply to @note#1648572368
The internet is no longer the Internet. What we call “the internet” now is basically how early television was in the in 60’s: you get three highly curated channels that tell you how to think and have nothing interesting on them.
The Internet hasn’t been about education in 20 years. Now it’s about selling stuff and receiving your daily dose of government propaganda. The Internet will continue to consume us until we’re fully enveloped in a simulated world.